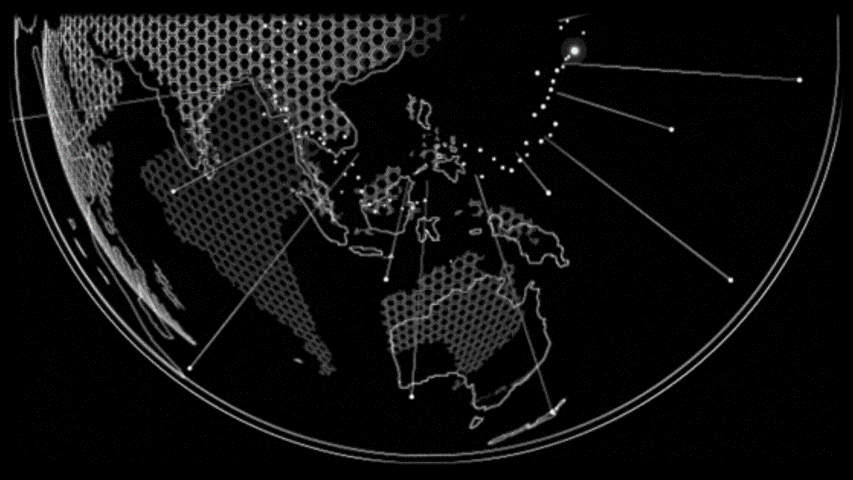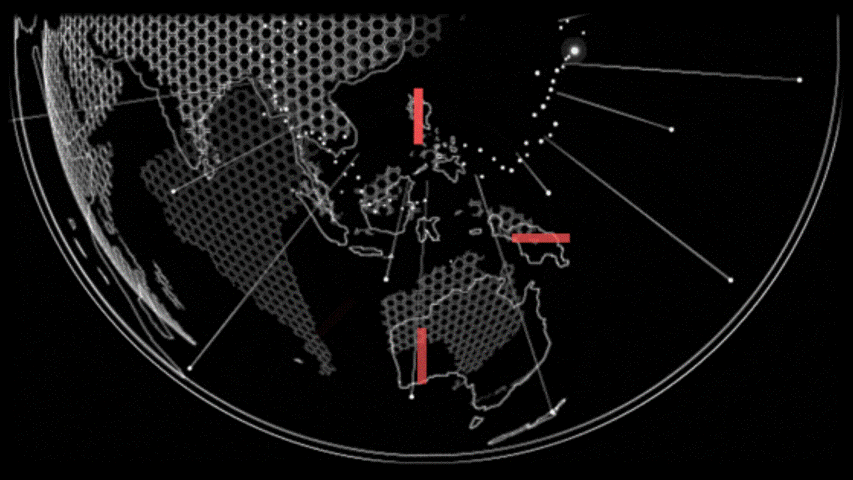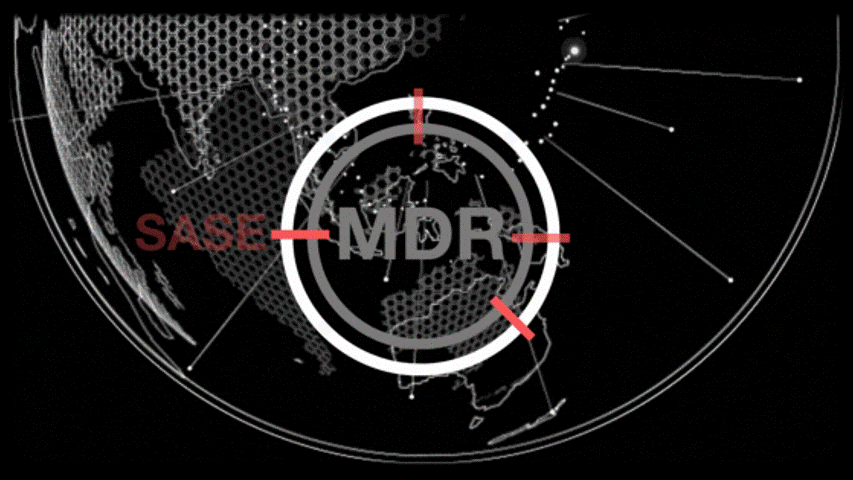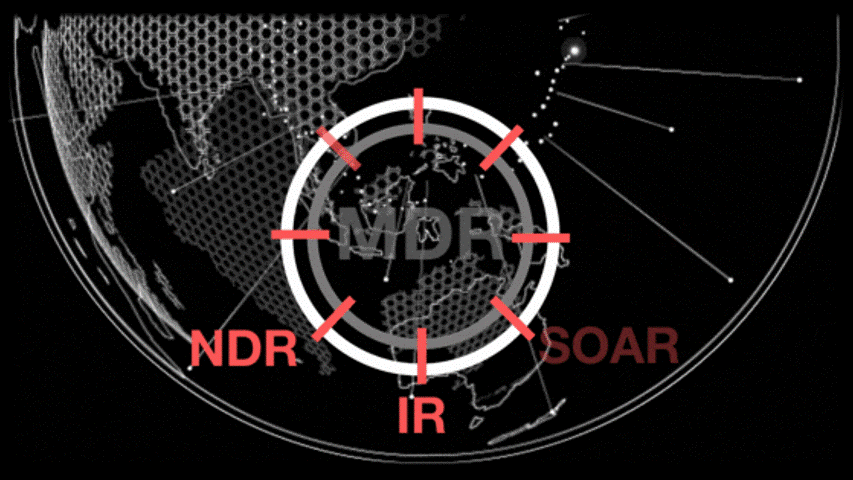
Managed Detection & Response
Power up your Cyber Defenses
Power up your Cyber Defenses
Organizations are currently experiencing an unparalleled level of cyber assaults, which are becoming more sophisticated and frequent. These attacks come from a range of threat actors, including nation-state and organized criminal groups. Given this reality, it’s not a matter of if you will be breached, but rather when it will occur and how you will react. In the current climate, using point products that lack central orchestration is inadequate. To meet the demands of today’s world, we have compiled a collection of the most powerful security tools available, which are fully integrated and managed by our team of world-class experts.
The A-Team
24/7/365

Organizations are currently experiencing an unparalleled level
of cyber assaults, which are becoming more sophisticated and
frequent. These attacks come from a range of threat actors, including nation-state and organized criminal groups. Given this reality, it’s not a matter of if you will be breached, but rather when it will occur and how you will react.
Secure global reach
Global
Five-Eyes
Locations


Manageable costs
Subscription
model

In the current climate, using point products that lack central
orchestration is inadequate. To meet the demands of today’s world, we have compiled a collection of the most powerful security tools available, which are fully integrated and managed by our team of world-class experts.reducing the likelihood of mistakes that could lead to security incidents.
The A-Team
24/7/365

Secure global reach

Global
Five-Eyes
Locations
Manageable costs
Subscription
Model


- +61 1300 105 473
- [email protected]
- 8 Ross Street, South Melbourne, VIC 3205
- 403/55 Holt Street, Surry Hills NSW 2010 (Sydney)
- 12 The Square, Market Harborough, UK
Company
Partners
- Palo Alto Networks
- Microsoft
- Cisco
- VMWare
- + All Partners
